Streamline Your Route to ANSSI Certification
The French National Cybersecurity Framework sets the national benchmark for cybersecurity governance and resilience in France, emphasising control, oversight, and response readiness across digital infrastructure. Secrato helps you align with ANSSI guidance through centralised risk management, continuous monitoring, and automated compliance oversight.
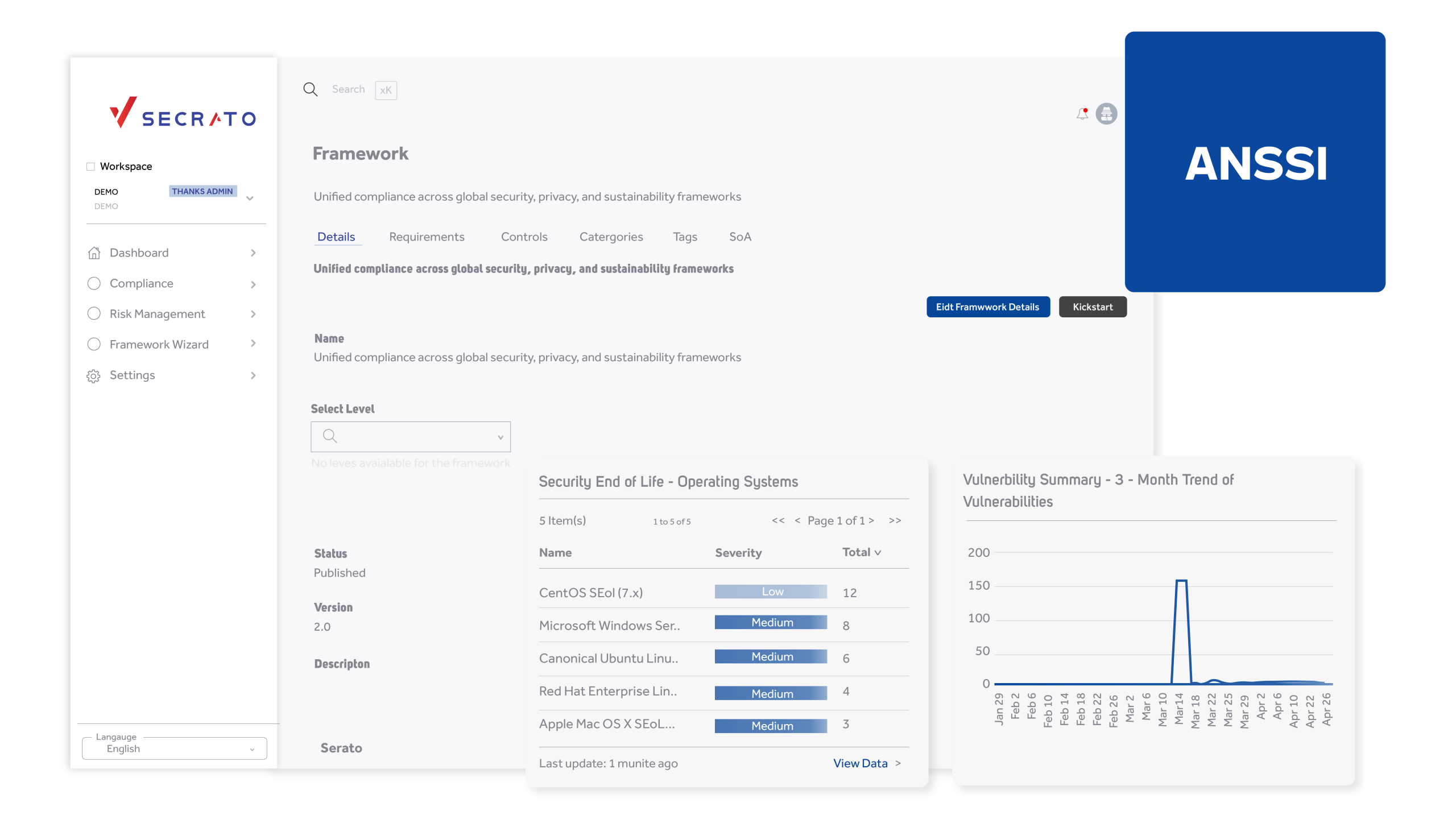
Demonstrate your organisation’s adherence to national cybersecurity standards. Secrato’s Trust Center enables you to share mapped controls, security policies, and real-time posture data securely with auditors or regulators, providing clear, verifiable evidence of compliance readiness.


Through Secrato’s framework library and evidence management, you can map ANSSI-aligned controls, policies, and documentation within a single secured workspace. Features like policy linking, version control, and role-based access ensure that evidence and control ownership are traceable and audit-ready at all times.
Secrato enhances your ANSSI compliance with continuous monitoring, ICT risk oversight, and automated alerting. Real-time dashboards track system maturity, control deviations, and remediation progress using widgets, timelines, and traffic-light indicators that make security posture instantly visible.

Centralize your audit process with a single source of truth for compliance evidence, findings, and remediation tracking.
Automatically link controls, assessments, and evidence across your compliance ecosystem so you’re always prepared for your next review.
Simplify compliance with automated workflows, real-time status tracking, and tailored reports for every framework.
Simplify policy creation with ready-made templates for every framework, a guided step-by-step builder to tailor policies to your organisation, and automated employee acceptance tracking.
Eliminates redundant work by harmonising controls across multiple compliance standards. With pre-mapped frameworks you can manage compliance once and apply it everywhere.
Secrato integrates with cloud providers, task trackers, and a growing set of selected technologies. Automate key workflows like access reviews, vulnerability tracking, and task syncing across platforms.
Audit-ready compliance, policies & proof in one place
Data-driven compliance for continuous readiness
Centralize, automate, and stay ahead of risks
Integrated policy control for consistent governance