Smarter Compliance. Stronger Cyber Resilience.
The National Institute of Standards and Technology Cybersecurity Framework series defines comprehensive guidelines for managing cybersecurity risk and resilience across information systems. Secrato helps you manage NIST 800 compliance with automated control assessments, centralised risk management, and continuous monitoring that strengthen both governance and assurance.
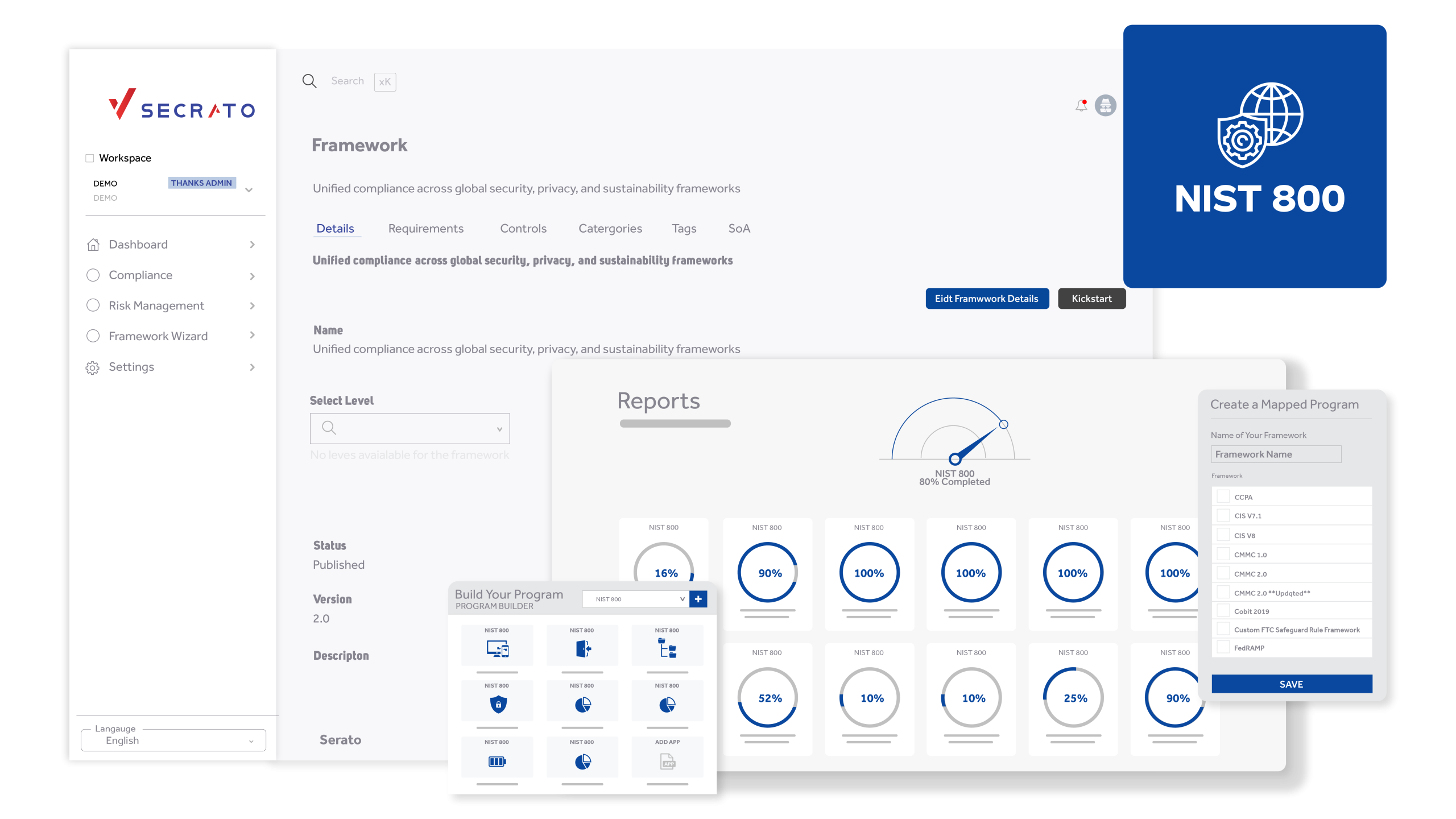
Secrato provides a structured environment to manage every NIST 800 control. Link evidence, ownership, and policies to each requirement and track performance through version-controlled documentation. Role-based access ensures accountability across teams while maintaining data integrity and auditability.


Secrato’s Risk Register integrates seamlessly with NIST 800 controls that allows you to score risk impact and assign ownership in real time. Automated linkage between failed controls and risk entries enables faster mitigation and transparent reporting to internal or external stakeholders.
Secrato enhances cybersecurity visibility with continuous control monitoring, deviation alerts, and timeline-based tracking. Teams can monitor control performance across domains, detect gaps early, and maintain consistent oversight without manual intervention.

Centralize your audit process with a single source of truth for compliance evidence, findings, and remediation tracking.
Automatically link controls, assessments, and evidence across your compliance ecosystem so you’re always prepared for your next review.
Simplify compliance with automated workflows, real-time status tracking, and tailored reports for every framework.
Simplify policy creation with ready-made templates for every framework, a guided step-by-step builder to tailor policies to your organisation, and automated employee acceptance tracking.
Eliminates redundant work by harmonising controls across multiple compliance standards. With pre-mapped frameworks you can manage compliance once and apply it everywhere.
Secrato integrates with cloud providers, task trackers, and a growing set of selected technologies. Automate key workflows like access reviews, vulnerability tracking, and task syncing across platforms.
Audit-ready compliance, policies & proof in one place
Data-driven compliance for continuous readiness
Centralize, automate, and stay ahead of risks
Integrated policy control for consistent governance