Safeguard Sensitive Data. Prove Compliance.
The Payment Card Industry Data Security Standard sets the global standard for protecting cardholder data and preventing payment-related breaches. With Secrato, you can strengthen trust in every transaction by automating control monitoring, validating evidence in real time, and proving compliance with confidence.
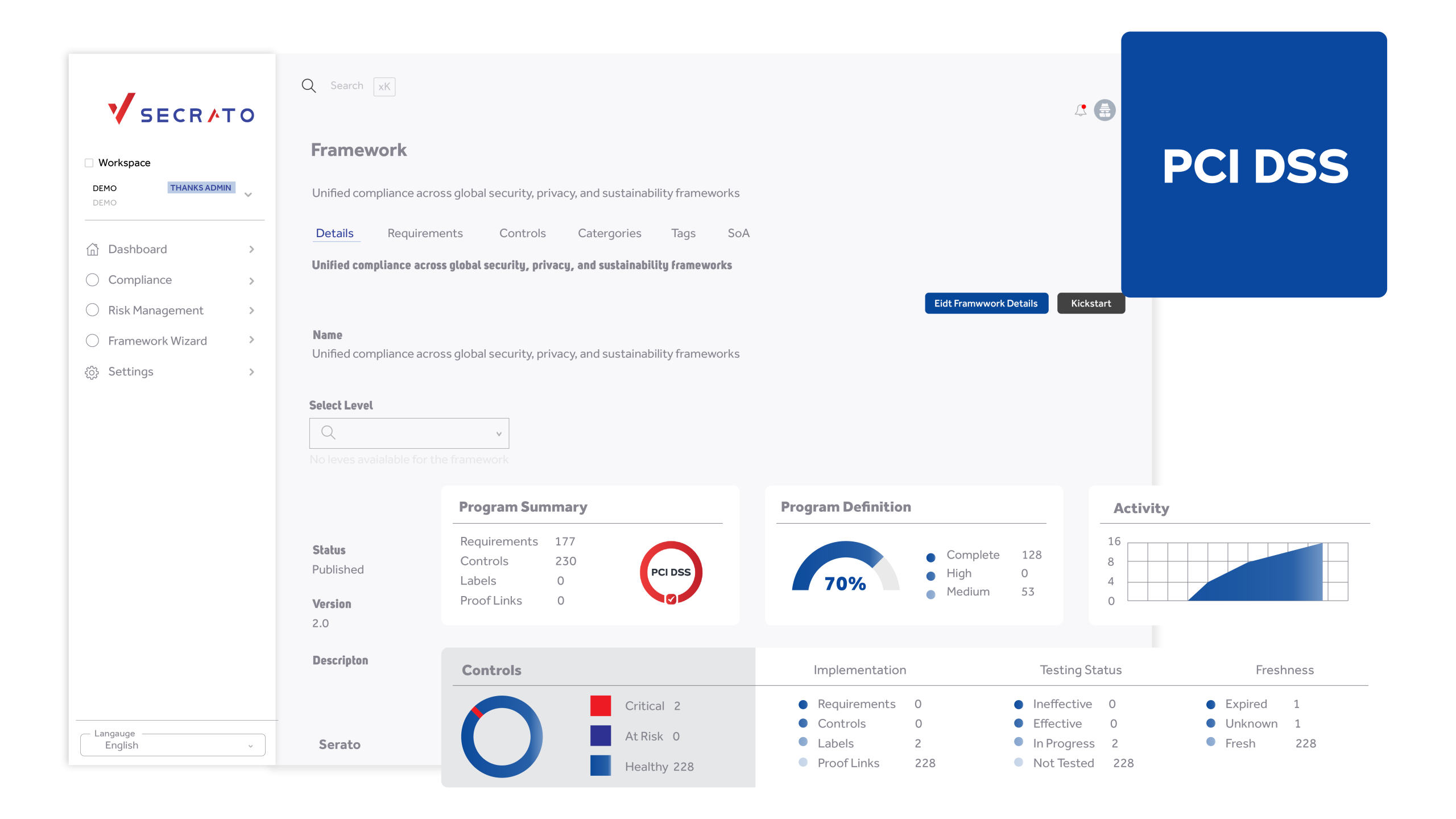
Clients trust you with their most sensitive data. Secrato makes it easy to show that trust is earned and maintained. All PCI DSS controls, policies, and evidence live in one place, keeping your security posture visible, organised, and audit-ready at any moment.


Empower your teams with clear governance. Secrato’s role-based access and workspace permissions define who can manage, approve, or review PCI DSS controls, eliminating overlaps and ensuring traceability for every action and document.
Payment compliance doesn’t end with certification — it grows with your business. Secrato supports multi-framework mapping and vendor integrations, connecting PCI DSS with ISO 27001, NIST 800, or DORA. Generate real-time dashboards, export audit-ready reports, and maintain continuous validation as your operations expand.

Centralize your audit process with a single source of truth for compliance evidence, findings, and remediation tracking.
Automatically link controls, assessments, and evidence across your compliance ecosystem so you’re always prepared for your next review.
Simplify compliance with automated workflows, real-time status tracking, and tailored reports for every framework.
Simplify policy creation with ready-made templates for every framework, a guided step-by-step builder to tailor policies to your organisation, and automated employee acceptance tracking.
Eliminates redundant work by harmonising controls across multiple compliance standards. With pre-mapped frameworks you can manage compliance once and apply it everywhere.
Secrato integrates with cloud providers, task trackers, and a growing set of selected technologies. Automate key workflows like access reviews, vulnerability tracking, and task syncing across platforms.
Audit-ready compliance, policies & proof in one place
Data-driven compliance for continuous readiness
Centralize, automate, and stay ahead of risks
Integrated policy control for consistent governance